Physical Layer Secrecy
The embedded nature of 5G networks imply not only power-limitation of devices, but also a likelihood that a greater share of traffic will include highly sensitive and personal information, which together call for new wireless security mechanisms that do not rely on the overhead-heavy and coordination-intense cryptographic protocols of today. Physical layer security is an upcoming research area that makes use of properties of the physical layer and seeks the possibility of achieving perfect secrecy in the wireless channel.
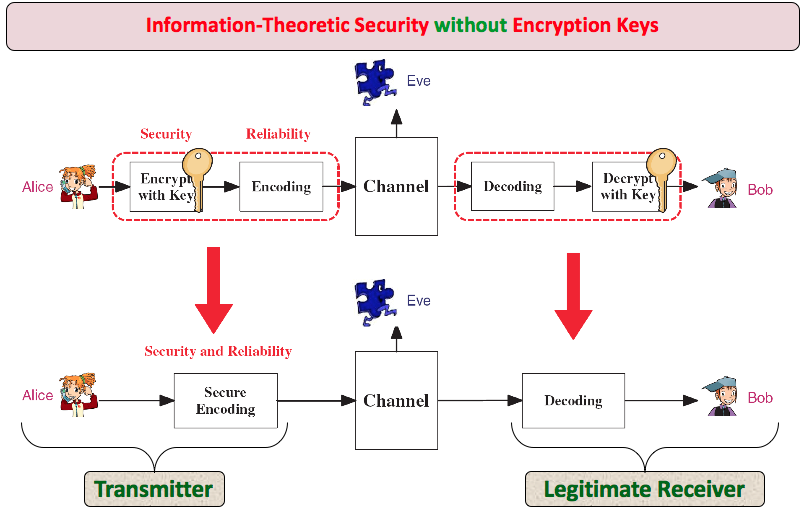
Physical layer security provides a set of mechanisms that makes use of the properties of the physical layer to make eavesdropping harder. It aims at exploiting the randomness which is inherent in noisy channels to provide an additional level of protection at the physical layer. It is also an upcoming research area that seeks the possibility of achieving perfect secrecy in wireless communications in the presence of eavesdroppers, while leaking minimum possible information to them. The interesting concept is to make use of physical layer characteristics to improve the security and reliability. Information theoretic security is a notion of measuring secrecy in communications system, which was based on Shannon's perfect secrecy. The foundations of information-theoretic security was laid by the work of Ozarow and Wyner, in which the term wire-tap channel was first coined in reference to the communication problem where an eavesdropper shares with the receiver full information on the encoding and randomization procedures introduced by the transmitter. After these breakthrough results, security started playing a role at physical layer along with traditional error correction coding mechanisms.
Research
Members Involved : S. Vuppala
In our group, we study the impact of topology and interference onto the physical layer wireless security of random networks. In particular, the locations of the base stations, users and eavesdropper nodes are modeled as independent two-dimensional Poisson point processes. We derive closed-form expressions for the secrecy rate distribution, average secrecy rate, secrecy outage probability, secrecy transmission capacity, etc., of such random networks under various fading channels (Rayleigh, Nakagami-m, Shadowing), and colluding eavesdroppers with and without considering correlated channels. We also analyze the impact of interference on the secrecy metrics of various random networks. Furthermore, we also perform analysis of the secrecy outage of random networks under the Matern Hard-core Point Process model, with the objective of shedding light on the security limitations/capabilities inherently encountered in cellular systems. We recently started our work on impact of blockages on PHY security in mmWave networks. We also characterize the use of fractional frequency from secrecy perspective in LTE systems.
PhD Theses
Physical layer security provides a set of mechanisms that makes use of the properties of the physical layer to make eavesdropping harder. It aims at exploiting the randomness which is inherent in noisy channels to provide an additional level of protection at the physical layer. It is also an upcoming research area that seeks the possibility of achieving perfect secrecy in wireless communications in the presence of eavesdroppers, while leaking minimum possible information to them. The interesting concept is to make use of physical layer characteristics to improve the security and reliability. Information theoretic security is a notion of measuring secrecy in communications system, which was based on Shannon's perfect secrecy. The foundations of information-theoretic security was laid by the work of Ozarow and Wyner, in which the term wire-tap channel was first coined in reference to the communication problem where an eavesdropper shares with the receiver full information on the encoding and randomization procedures introduced by the transmitter. After these breakthrough results, security started playing a role at physical layer along with traditional error correction coding mechanisms.
Research
Members Involved : S. Vuppala
In our group, we study the impact of topology and interference onto the physical layer wireless security of random networks. In particular, the locations of the base stations, users and eavesdropper nodes are modeled as independent two-dimensional Poisson point processes. We derive closed-form expressions for the secrecy rate distribution, average secrecy rate, secrecy outage probability, secrecy transmission capacity, etc., of such random networks under various fading channels (Rayleigh, Nakagami-m, Shadowing), and colluding eavesdroppers with and without considering correlated channels. We also analyze the impact of interference on the secrecy metrics of various random networks. Furthermore, we also perform analysis of the secrecy outage of random networks under the Matern Hard-core Point Process model, with the objective of shedding light on the security limitations/capabilities inherently encountered in cellular systems. We recently started our work on impact of blockages on PHY security in mmWave networks. We also characterize the use of fractional frequency from secrecy perspective in LTE systems.
PhD Theses
- Md. Z. I. Sarkar, Information-Theoretic Security in Wireless Communication Systems, Feb. 2012.
- W. Liu, Enhancing Physical Layer Security in Wireless Networks with Cooperative Approaches, June 2016.
- S. Vuppala, S. Biswas and T. Ratnarajah, "Secrecy Outage Analysis of k-th Best Link in Random Wireless Networks," IEEE Trans. on Communications, Vol. 65, Issue 10, pp. 4478-4491, Oct. 2017.
- S.Vuppala, S. Biswas and T. Ratnarajah, "An Analysis on Secure Communication in Millimeter/Micro-Wave Hybrid Networks", IEEE Trans. on Communications, Vol. 64, No. 8, pp. 3507-3519, Aug. 2016.
- W. Liu, Z. Ding, T. Ratnarajah, and J. Xue, "On Ergodic Secrecy Capacity of Random Wireless Networks with Protected Zones," IEEE Trans. on Vehicular Technology, Vol. 65, No. 8, pp.6146-6158, August 2016..
- W. Liu, M. Z. I. Sarkar, T. Ratnarajah and H. Du, "Securing Cognitive Radio with a Combined Approach of Beamforming and Cooperative Jamming," IET Communications, Sep. 2016.
- S. Vuppala, S. Biswas, T Ratnarajah, “Analysis of Secure Communication in Millimeter Wave Networks: Are Blockages Beneficial?,” in proc, ICASSP, Shanghai, China, Mar., 2016.
- S. Vuppala, S. Biswas, T Ratnarajah, “On the Security Region of Best Source Indices in Random Wireless Networks”, in proc, IEEE ICC, Kuala Lumpur, Malaysia, May, 2016.
- S. Vuppala, W. Liu, T Ratnarajah and G. Abreu, “Secrecy Outage of Nakagami-m MISO Channels with Randomly Located Receivers”, Proc. IEEE International Conference on Communications (ICC), London, UK, June 2015.
- S. Vuppala, W. Liu, T Ratnarajah and G. Abreu, “Secrecy outage analysis of cognitive wireless sensor networks,” Proc. IEEE Fourty-Eigth Asilomar Conference on Signals, Systems, and Computers (ASILOMAR), Pacific Grove, CA, Nov. 2014. (Best paper award nominee)
- S. Vuppala, W. Liu, T Ratnarajah, and G. Abreu, “Secrecy Outage in Correlated Nakagami-m Fading Channels”, Proc. IEEE Personal Indoor Mobile Radio Communication (PIMRC), Sept. 2014.
- M. Z. I. Sarkar, T. Ratnarajah, and Z. Ding, "Beamforming with Opportunistic Relaying for Wireless Security" IEE Proc. Communications, Vol. 8, Iss. 8, pp. 1198-1210, 2014 [Special Issue: Secure Physical Layer Communications].
- M. Z. I. Sarkar and T. Ratnarajah, "Enhancing Security in Correlated Channel with Maximal Ratio Combining Diversity," IEEE Trans. on Signal Processing, Vol. 60, No. 12, pp. 6745-6751, Dec. 2012.
- M. Z. I. Sarkar and T. Ratnarajah, “Aspect of Security in the Cognitive Relay Assisted Interference Channels,” In Proc. IEEE Workshop on Information Theory, Lausanne, Switzerland, Sep. 03-07, 2012.
- M. Z. I. Sarkar and T. Ratnarajah, “Enhancing Security in the Cognitive Relay Assisted Co-existing Radio Systems with Interferences,” In Proc. the IEEE International Conference on Communications, Budapest, Hungary, June 9-13, 2013.